Configuring SAML SSO for Salesforce
Accops let users to Single Sign-On into Salesforce account with one set of login credentials, eliminating user-managed passwords and the risk of phishing. Salesforce Single Sign-On set up leverages the existing on-premise Active Directory infrastructure and provides seamless integration without the need to manage multiple on-premise and cloud identities.
Environment#
- Accops HySecure Gateway v5299, v5360, v6026 onwards
- Salseforce Tenant
Pre-Requisites#
- Salesforce Admin Portal Access.
- Accops HySecure Gateway with Public DNS name and valid SSL Certificate.
- Managenent console of HySecure Gateway using Secirity Officer Account.
- Shell Access to Hysecure Gateway.
Configurations#
Steps to setup Salesforce in Accops (Identity Provider)#
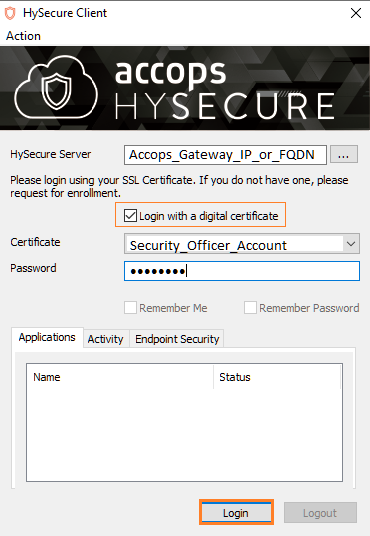
Step 1: Login with a digital certificate in Accops HySecure Gateway using Security Officer Account.
Step 2: Go to "Access Management >> Applications >> Add" .
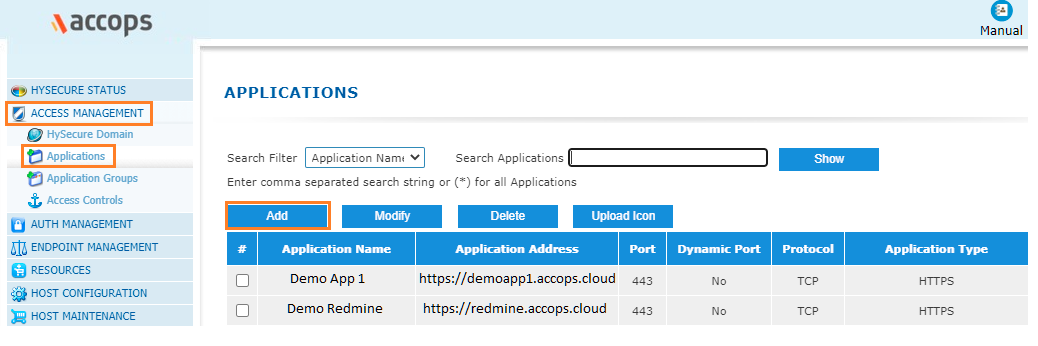
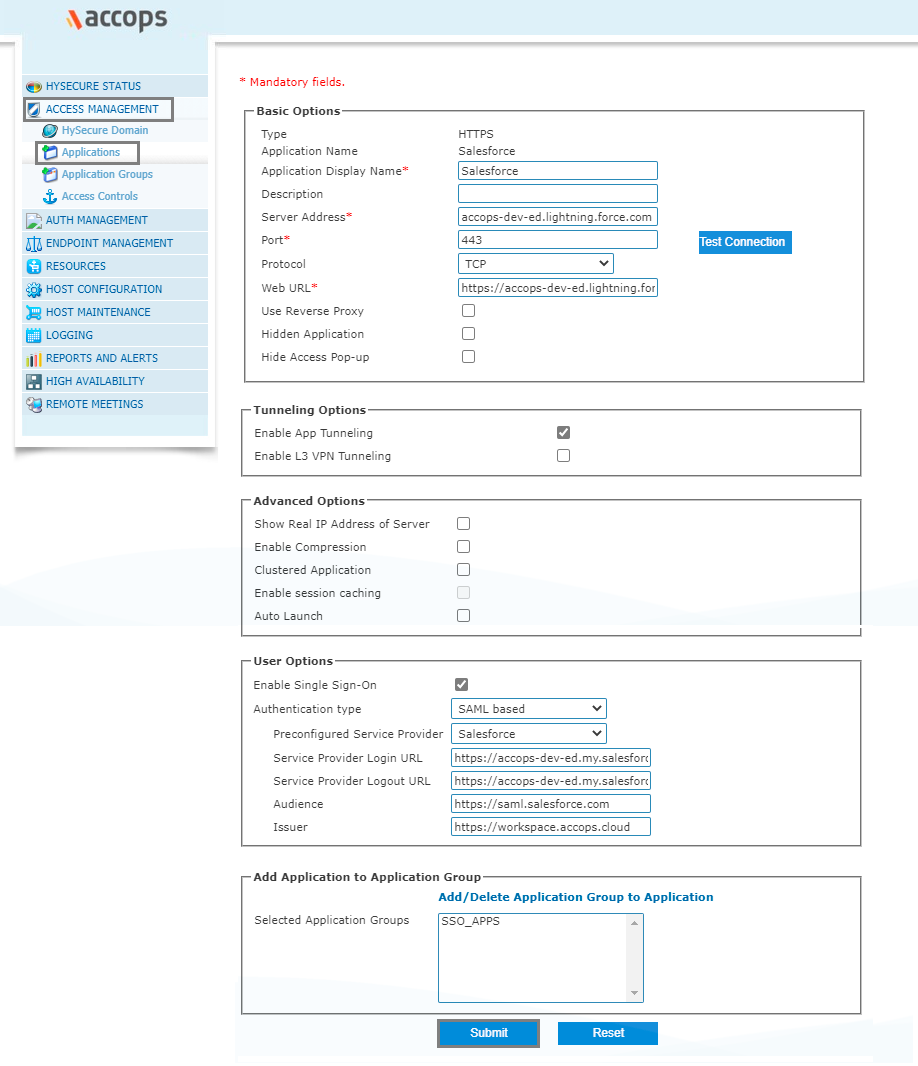
Step 3: Click on Add button to create new application as "Salesforce".
note
Go to Salesforce Portal https://login.salesforce.com/ and login with your GLobal Admin and get the info of Salesforce Tenant.
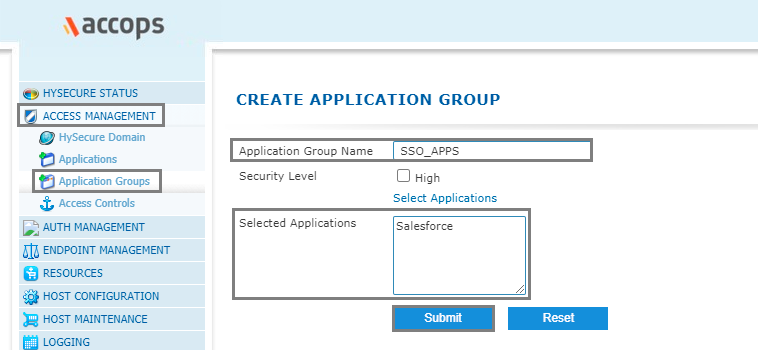
Step 4: Add Salesforce app into New/Existing Application Groups.
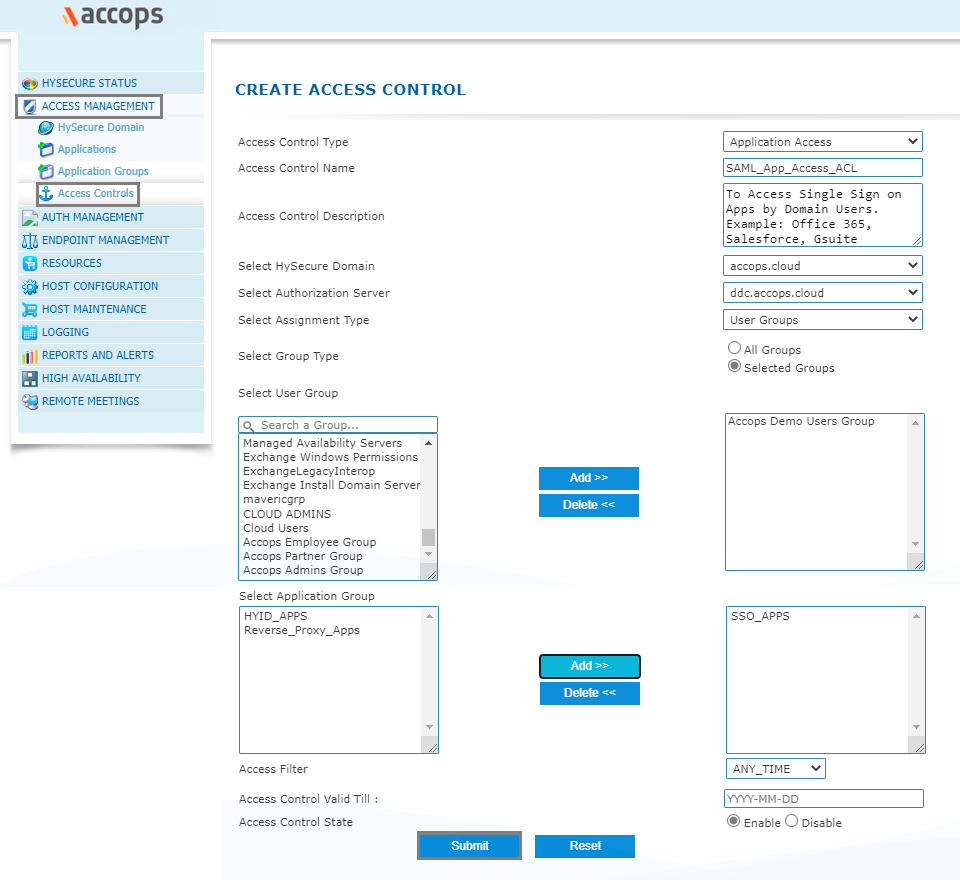
Step 5: Create/Update an "Application Access" in New/Exisitng "Access Controls"
Step 6: Verify SAML SSO Certificate in Accops HySecure Gateway.
Please ensure below files availability in Accops HySecure Gateway.
note
If above files are not present then, Create it using below command
Step 7: Copy the content of SAML SSO Certificate SAML_Signing_Certificate form Accops Gateway.
note
Please ensure while copying the content there aren't any new line in SAML SSO Certificate.
Steps to setup Accops in Salesforce (Service Provider)#
Step 1: Go to to Salesforce https://login.salesforce.com or https://domain.my.salesforce.com with Admin Access.
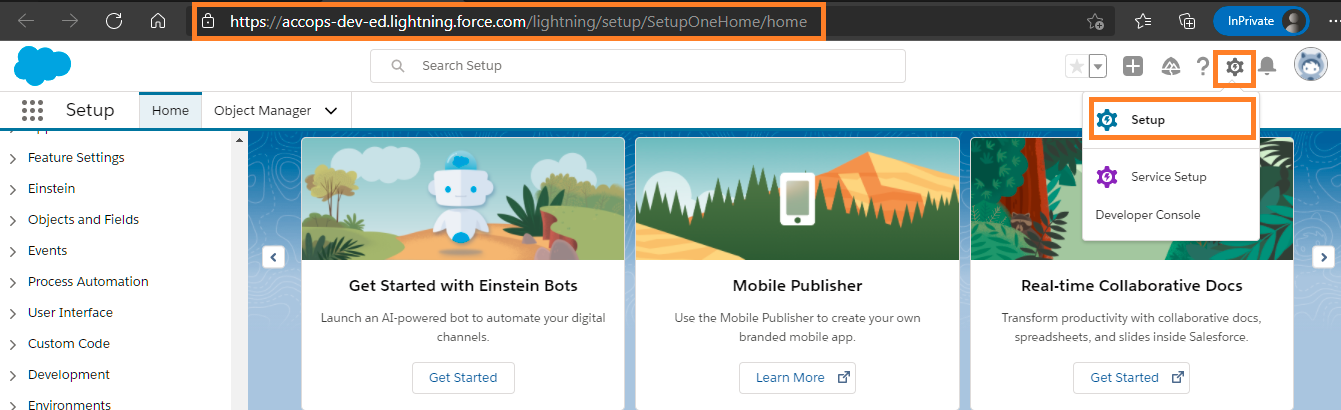
Step 2: After Login to Salesforce Portal, Go to Settings.
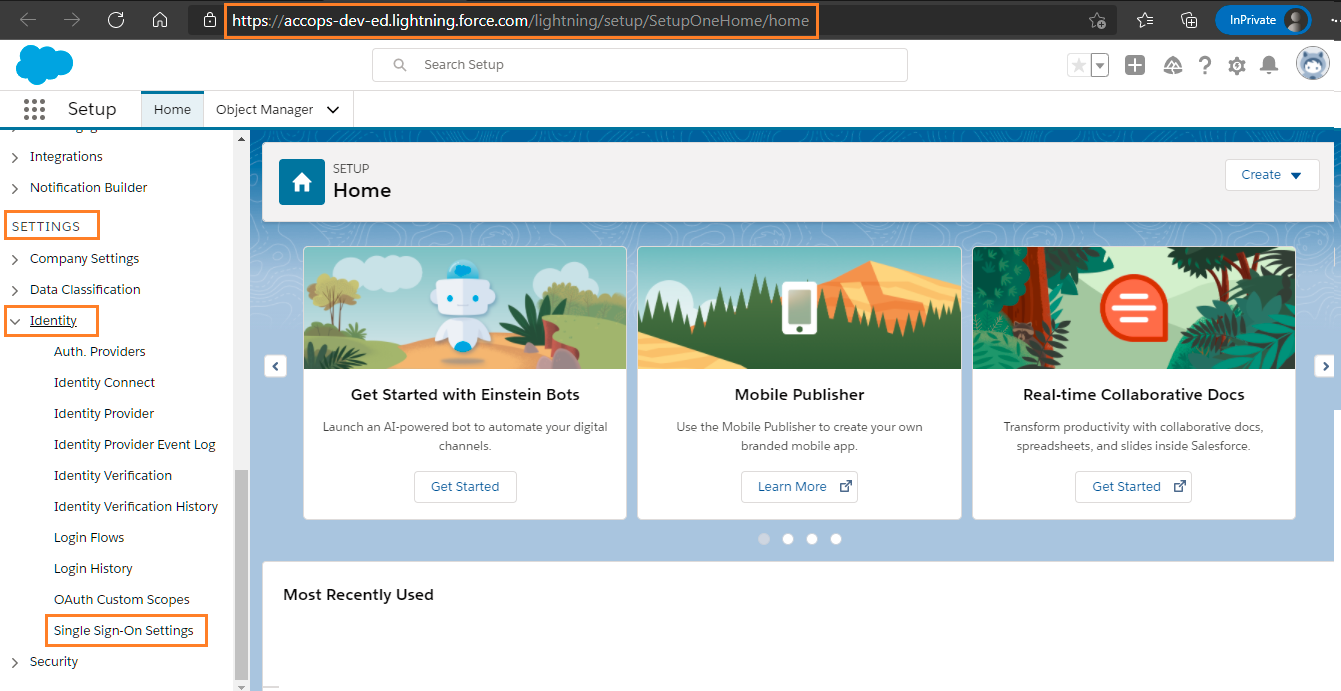
Step 3: Go to Settings >> Identity >> Single Sign-On Settings.
Step 4: Click on New
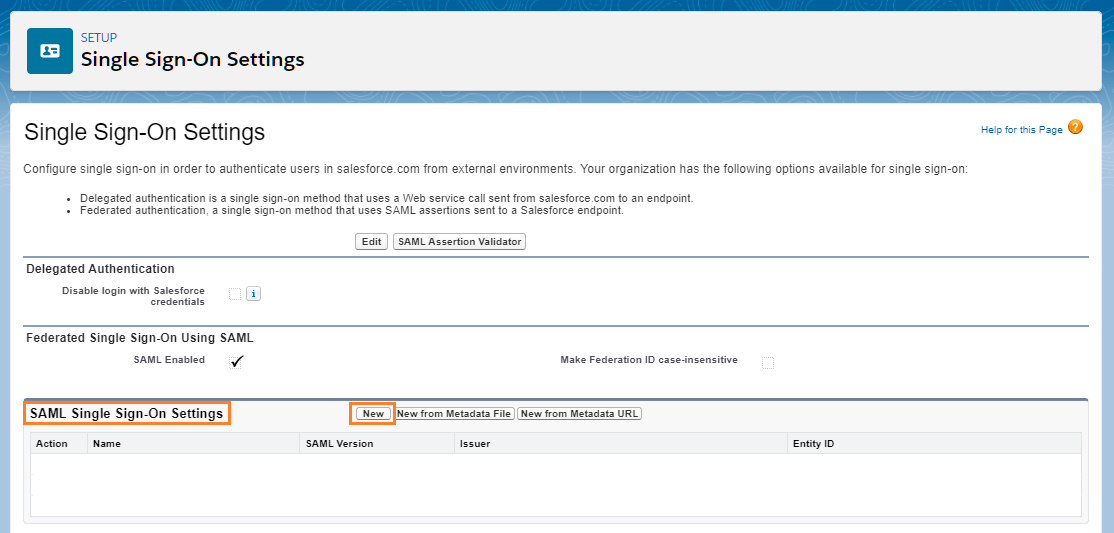
Step 5: Fill the Required Details.
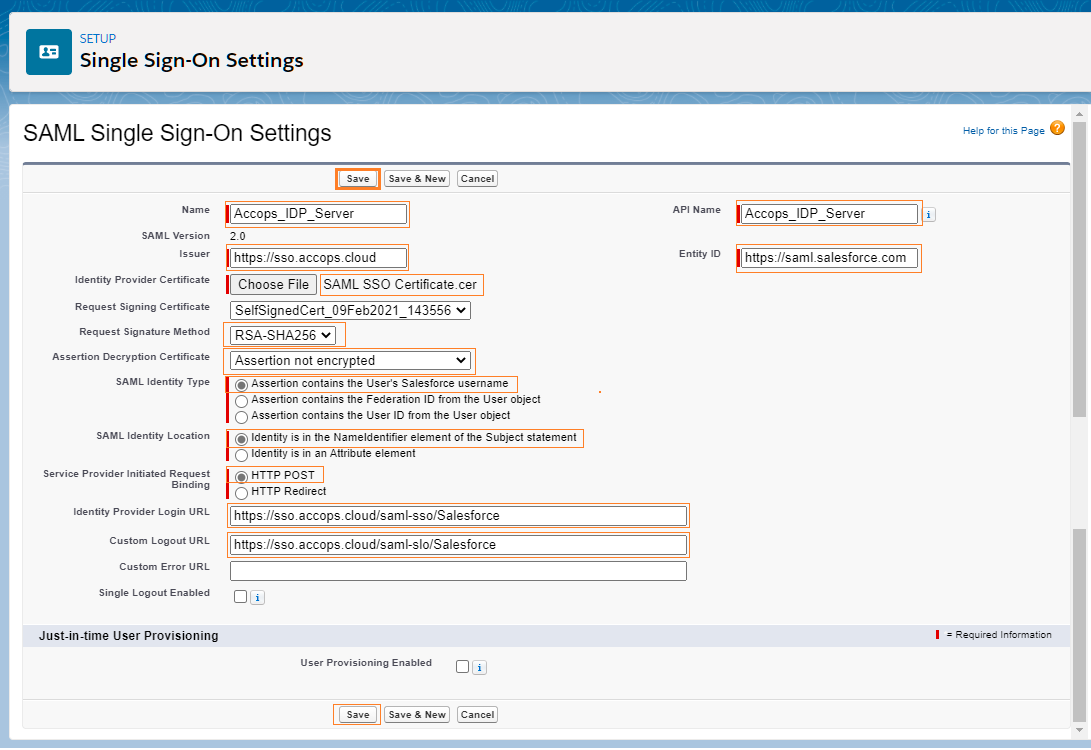
Step 5: Verify the IDP Settings and Endpoint details of Salesforce.
- Your Organization Login URL https://accops-dev-ed.my.salesforce.com Logout URL https://accops-dev-ed.my.salesforce.com/services/auth/sp/saml2/logout
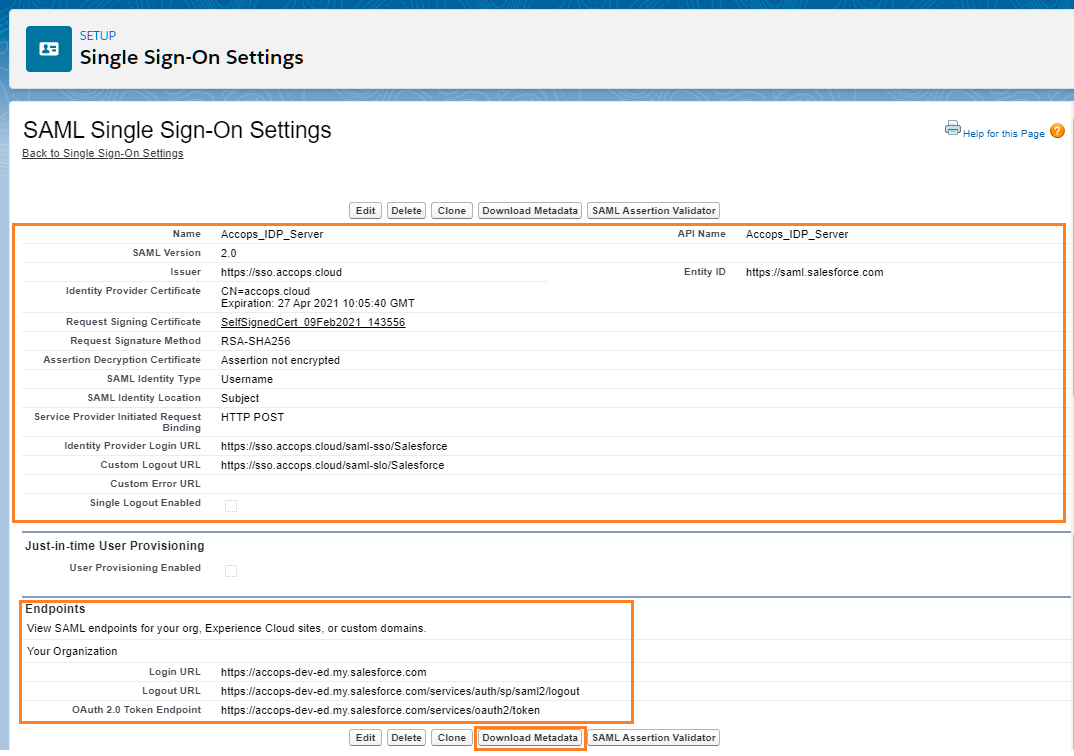
Click on Download Metadata to Configure the Identity Provider Server, If it is not configured
Sign in to your Salesforce#
Using IDP initiated login#
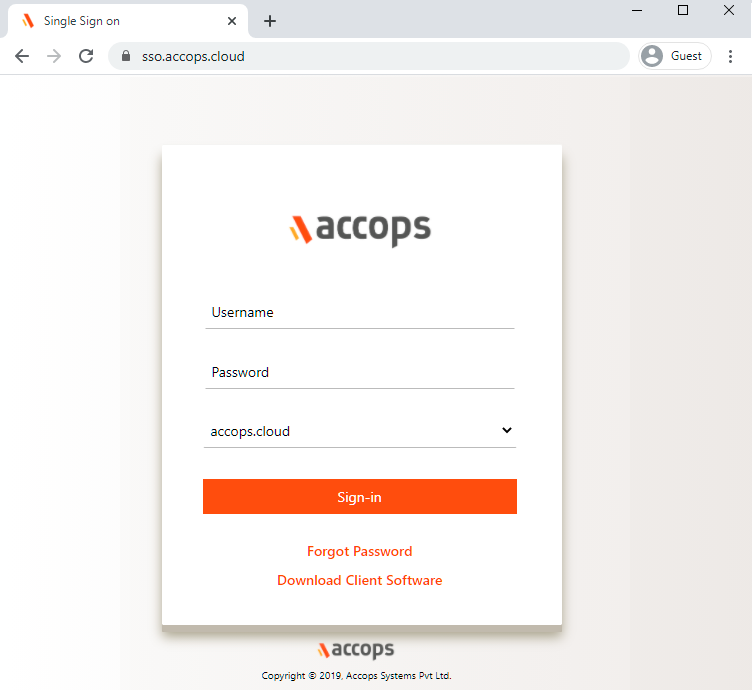
- Go to Accops Workspace Portal (https://sso.accops.cloud)
Enter Your Login Credentials, Choose domain from dropdown and click on Sign In.
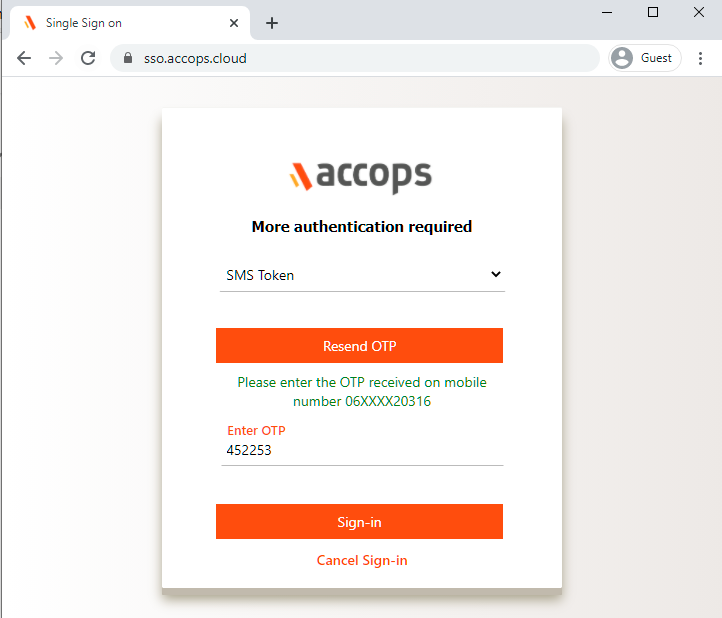
Verify yourself using Multi-Factor Autentcication by choosing the type of MFA from dropdown.
Post successful Autentication and Authorization User will will be redirected to Accops Workspace Portal.

click on Salesforce icon to launch Single Sign On access to Salsefore Portal.
Using SP initiated login#
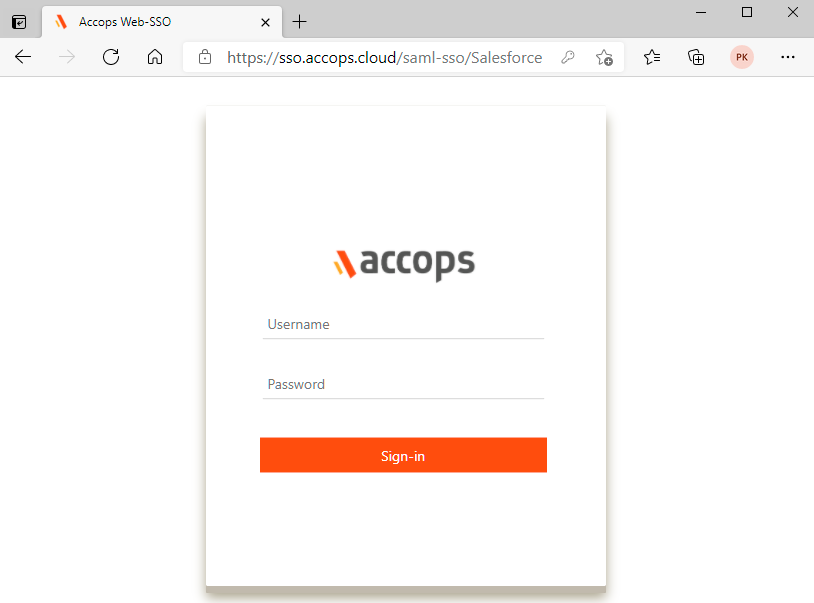
Go to to Salesforce https://accops-dev-ed.my.salesforce.com and select Login using Accops SSO

Autentication request will be redirected to Organization Sign in Page (Accops IDP Login Portal), Enter Authentication details and click on Sign-In.
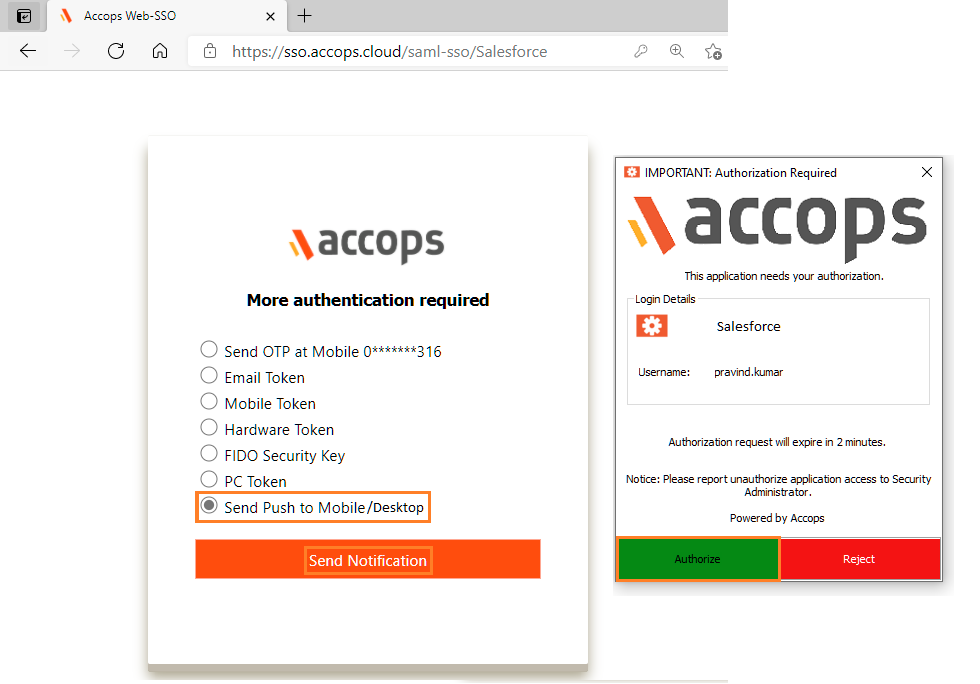
On Below Screen, Accops IDP Server will Prompt More Authenication required, Choose Send Push to Mobile/Desktop and Authorize the Desktop Push to Login.
Access Salesforce Portal.

Help/Support#
Please send a mail to support@accops.com for further help/Support.